Introduction: Modern Identity for Azure Virtual Desktop
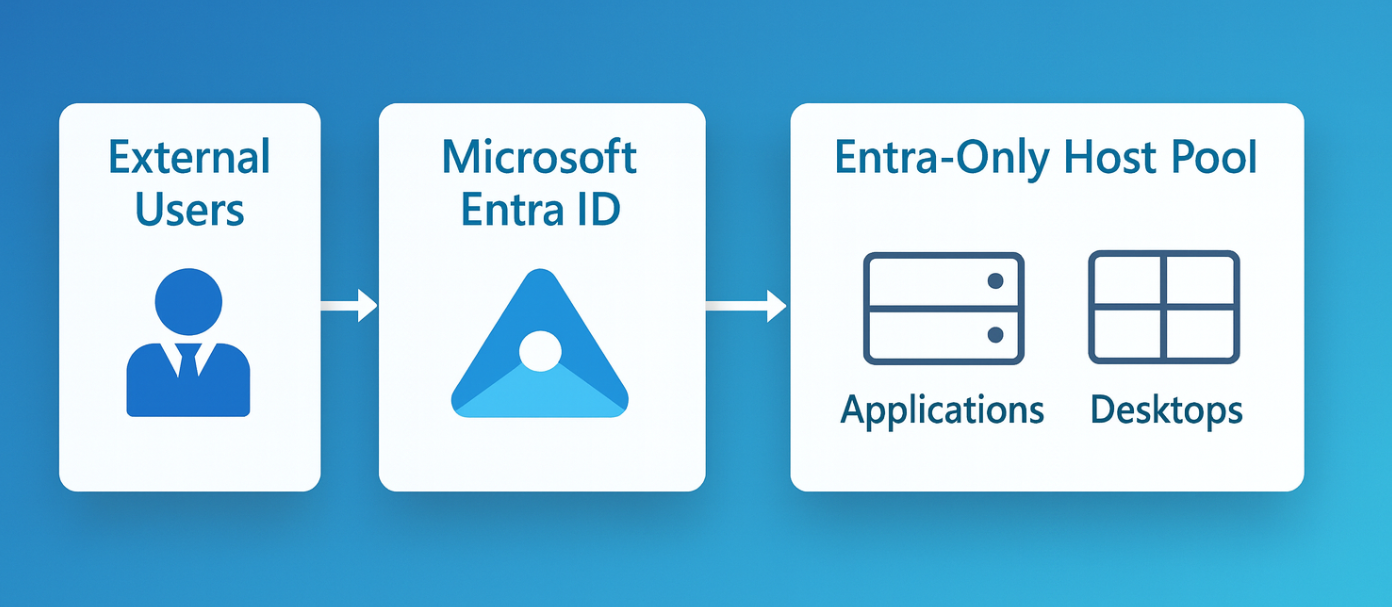
The world of remote work is evolving — and so is identity management. Microsoft’s latest preview update for Azure Virtual Desktop (AVD) introduces support for external identities without FSLogix, powered by Microsoft Entra ID (formerly Azure Active Directory).
External Identity Support in AVD allows users outside your Azure AD tenant to connect to your virtual desktops or published apps using their own organization’s credentials — with full Microsoft Entra ID authentication and Conditional Access enforcement.
Requirements for External Identity Preview
Session host operating system: The session host must be running Windows 11 Enterprise, versions 24H2 or later with the 2025-09 Cumulative Updates for Windows 11 (KB5065789) or later installed.
Session host join type: The session host must be Entra joined.
Single sign-on: Single sign-on must be configured for the host pool.
Windows App client: The external identity must connect from the Windows App on Windows or a web browser.
Limitations of External Identity Preview
FSLogix: FSLogix isn't supported yet. External identities can connect to a pooled resource, but will create a new user profile on each session host they sign in to.
Intune device configuration policies: Device configuration policies assigned to the external identity won't be applied to the user on the session host. Instead, assign device configuration policies to the device.
Cloud availability: This feature is only available in the Azure public cloud, but not the Government cloud or Azure operated by 21Vianet.
Cross cloud invites: Cross-cloud users aren't supported. You can only provide Azure Virtual Desktop resource access to users you invite from social identity providers, Microsoft Entra users from the Microsoft Azure commercial cloud or other identity providers registered in your workforce tenant. You can't assign Azure Virtual Desktop resources for users you invite from Microsoft Azure Government or Microsoft Azure operated by 21Vianet.
Token protection: Microsoft Entra has certain limitations for token protection for external identities. Learn more about Windows App support for token protection by platform.
Kerberos authentication: External identities can't authenticate to on-premises resources using Kerberos or NTLM protocols.
Windows App clients: When using the Windows App on Windows, you must set a registry key on the device running the Windows App to complete the B2B login. Learn more about the required registry key.
See Microsoft Entra B2B best practices for recommendations on configuring your environment for external identities and Licensing for licensing guidance.
Azure Academy Video Tutorial
How Authentication Works for External Users
Step-by-Step Flow
- The admin shares an AVD workspace URL or invitation.
- The external user logs in using their own tenant credentials.
- The home tenant authenticates the user via Entra ID.
- Access policies from the resource tenant are applied.
- The user launches the desktop/app session — no FSLogix required.
Integration with Microsoft Entra B2B
This feature relies on Azure AD B2B collaboration, so users from any Microsoft Entra tenant can be granted access via invitation or group assignment.
Security Benefits
Zero Trust Architecture
- Every connection is validated via Microsoft Entra Conditional Access and risk-based policies.
Simplified Governance
- External users authenticate via their own tenant; no need to manage external passwords or accounts.
Easy Offboarding
- Removing a B2B collaboration link instantly revokes access — no local account cleanup required.
Use Cases for External Identity in AVD
- Contractor Access – Temporary access to secure internal systems.
- Training Environments – Offer short-term virtual sessions to learners.
- Multi-Tenant Collaboration – Provide controlled app access to partners.
FAQs
1️⃣ Can I use FSLogix with External Identities?
No. In this preview, sessions are stateless and FSLogix is not supported.
2️⃣ Is a domain join required?
No — only Microsoft Entra ID join is supported for external users.
3️⃣ Do external users need a Microsoft account?
Yes, they must belong to a Microsoft Entra tenant or use a Microsoft Account (MSA).
4️⃣ How is data protected?
Access is secured through Entra Conditional Access, encryption, and Zero Trust principles.
5️⃣ Is there extra licensing cost?
External users require a valid AVD or M365 license — but no separate AVD fee applies.
6️⃣ How does this differ from Windows 365?
AVD is session-based and scalable; Windows 365 offers personal, persistent Cloud PCs.
Conclusion: A Step Toward Entra-Native, Simplified Access
The External Identity (Preview) feature in Azure Virtual Desktop represents a huge leap forward in simplifying secure collaboration. B
Whether you're onboarding contractors, vendors, or training users — AVD’s External Identity support provides secure, compliant, and frictionless access with cloud simplicity.
🔗 External Links
- Azure Virtual Desktop Authentication (Microsoft Docs)
- Microsoft Entra External ID Overview
- Windows 365 Identity Comparison
- YouTube: AVD External Identities Preview Overview
Click Here To Return To Blog